Suspected North Korean hackers have moved 12 bitcoins, worth about $140,000, from one of the 280 cryptocurrency accounts the U.S. Department of Justice has targeted for seizure.
The transaction was spotted by cryptocurrency transaction monitor Whale Alert, with the service pointing out that one of the inputs in the transaction “has been listed by the U.S. government as forfeited. It is unclear who made the transaction.”
In a civil forfeiture complaint, the Department of Justice alleges the accounts were used by hackers tied to the North Korean government to launder millions of dollars worth of cryptocurrency stolen in several hacks in 2019.
The U.S. government alleges the funds hep Pyongyang undermine sanctions and sponsor its own program developing weapons of mass destruction. In a follow-up tweet, Whale Alert detailed the forfeited address could be a Huobi deposit address that received 2.97 BTC “a few days ago.” Per the service, the “address was sept” on August 31 “together with deposits made by other users.”
The DOJ’s complaint details three cryptocurrency heists that occurred last year. In one $272,000 worth of altcoins were stolen, while in the second one $2.5 million worth of multiple cryptoassets were stolen.
The third attack, which appears to be the hack that Singapore-based exchange CoinTiger suffered last year, saw hackers steal over 400 million Proton Tokens (PTT). While the exchange managed to stop 280 million PTT from being transferred out, 120 million tokens were traded out.
The next day CoinTiger reported losses of several other cryptocurrencies, which were laundered through a complicated series of transactions summarized in the complaint:
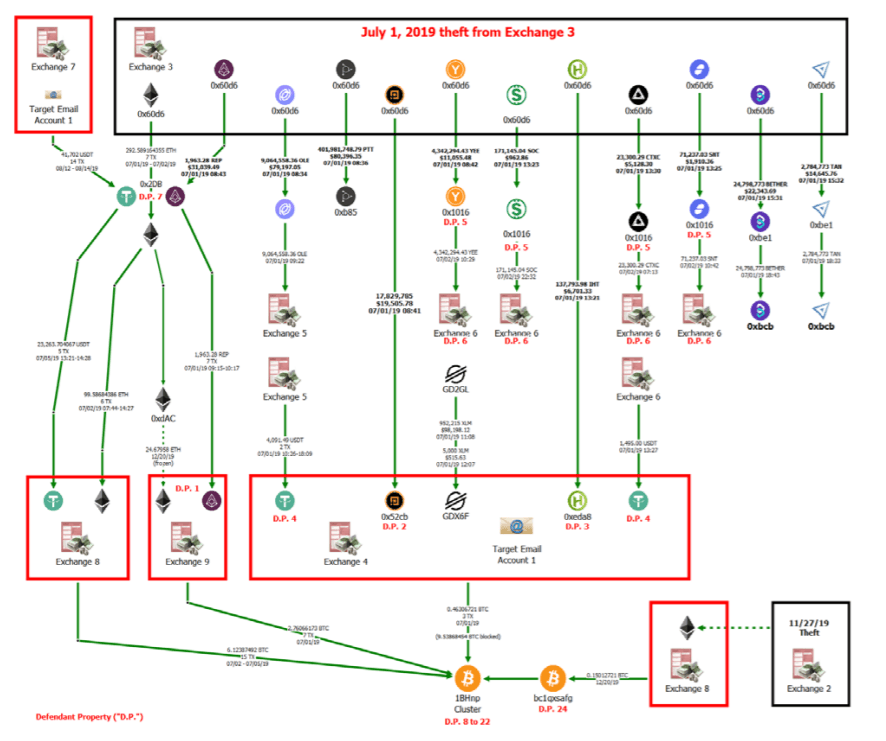
Chinese over-the-counter (OTC) traders reportedly helped the North Korean hackers launder the funds, which were initially moved on the blockchain using a technique known as “chain hopping,” whereby one form of crypto is transferred into another to hide their tracks.
Daniel Fort, the Internal Revenue (IRS) Criminal Investigation chief, said:
Despite the highly sophisticated laundering techniques used, IRS-CI’s Cybercrimes Unit was able to successfully trace stolen funds directly back to North Korean actors
The 280 cryptocurrency addresses were frozen after the DOJ filed a lawsuit to seize the funds, which are believed to be of over $250 million from hacks to “over a dozen virtual exchanges.” The DOJ also notably alluded to the existence of a “Cryptocurrency Strike Force, which was credited by Acting U.S. Attorney Michael Sherwin with playing a key role in the investigations.
As CryptoGlobe reported, in late 2018 a report by leading crypto security firm Group-IB revealed a hacking group tied to North Korea, the Lazarus group, was believed to have stolen $571 million in crypto from exchanges.
Featured image via Pixabay.









